
Winter Vivern APT Targets European Government Entities with Zimbra Vulnerabilities
[ad_1]
Advanced persistent threat actors (APTs) are known as Winter Viverns it is now targeting officials in Europe and the US as part of its ongoing cyber espionage campaign.
“TA473 since at least February 2023 has continued to exploit an unpatched Zimbra vulnerability in public-facing webmail portals that allowed them to gain access to the email mailboxes of government entities in Europe,” Proofpoint said in a new report.
The company’s security firm is tracking activity under its own moniker TA473 (aka UAC-0114), describing it as an enemy crew whose operations aligned with Russia’s and Belarusian geopolitical objectives.
What it lacks in sophistication, it makes up for in persistence. In recent months, the group has been linked to attacks targeting Ukrainian and Polish state authorities as well as government officials in India, Lithuania, Slovakia and the Vatican.
The NATO-related intrusion wave required the exploit CVE-2022-27926 (CVSS score: 6.1), a medium-severity security flaw now patched in Zimbra Collaboration that could allow an unauthenticated attacker to execute arbitrary JavaScript or HTML code.
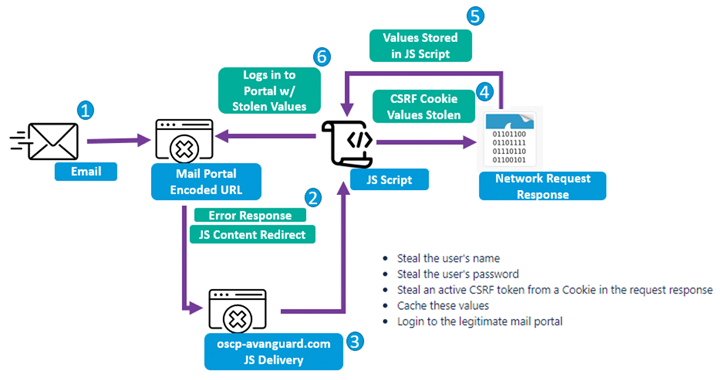
It also involves using a scanning tool such as Acunetix to identify unpatched webmail portals belonging to targeted organizations with the aim of sending phishing emails under the guise of friendly government agencies.
The message comes with a trap URL that exploits a cross-site scripting (XSS) weakness in Zimbra to execute a payload of custom Base64 encoded JavaScript within the victim’s webmail portal to extract usernames, passwords, and access tokens.
It should be noted that each JavaScript payload is tailored to the targeted web email portal, indicating that threat actors are willing to invest time and resources to reduce the likelihood of detection.
“TA473’s persistent approach to vulnerability scanning and exploitation of unpatched vulnerabilities impacting public-facing webmail portals was a key factor in this actor’s success,” said Proofpoint.
“The group’s focus on continuous reconnaissance and painstaking study of publicly exposed webmail portals to reverse-engineer JavaScript capable of stealing usernames, passwords, and CSRF tokens demonstrates its investment in compromising specific targets.”
Findings come in the middle revelation that at least three Russian intelligence agencies, including the FSB, GRU (associated with Sandworm), and SVR (associated with APT29), likely used hacking software and tools developed by a Moscow-based IT contractor called NTC Vulkan.
Become an Incident Response Pro!
Unlock the secrets to bulletproof incident response – Master a 6-Phase process with Asaf Perlman, Cynet’s Lead IR!
This includes frameworks such as Scan (to facilitate large-scale data collection), Amesit (to conduct information operations and manipulate public opinion), and Krystal-2B (to simulate coordinated IO/OT attacks against rail and pipeline control systems).
“Krystal-2B is a training platform that simulates OT attacks against different types of OT environments in coordination with multiple IO components by leveraging Amesit ‘for jamming purposes,'” Google’s Mandiant said.
“The projects contracted to from NTC Vulkan provide insight into investments by Russian intelligence services to develop capabilities to deploy operations more efficiently early in the attack lifecycle, a part of operations that is often hidden from our view,” the threat intelligence firm added.
[ad_2]
Source link






