
Hackers Use Self-Extracting Archives Exploit for Stealthy Backdoor Attacks
[ad_1]
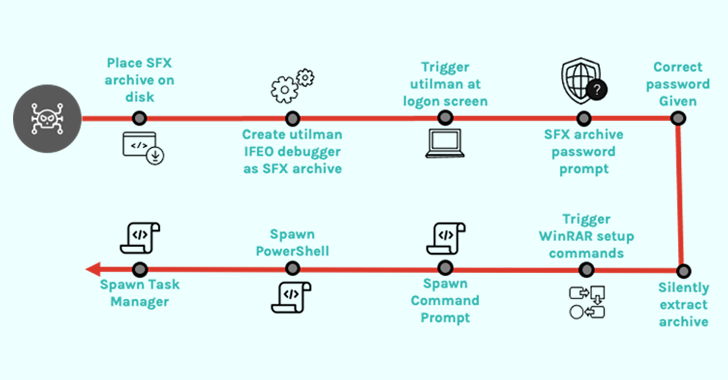
Unknown threat actors use malicious self-extracting archives (SFX) in an attempt to create persistent backdoor access to the victim’s environment, new findings from the CrowdStrike event.
SFX files are capable of extracting the data contained within them without the need for special software to display the file contents. This is achieved by including the decompressor stub, a piece of code that is executed to unpack the archive.
“However, SFX archive files can also contain hidden malicious functionality that may not be immediately visible to the recipient of the file, and can be missed only by technology-based detection,” CrowdStrike researcher Jai Minton said.
In a case investigated by the cybersecurity firm, the compromised credentials to the system were used to run a legitimate Windows accessibility application called Utility Manager (utilman.exe) and then launch a password protected SFX file.
This, in turn, is made possible by configure the debugger program (another executable) in the Windows Registry to a specific program (in this case, utilman.exe) so that the debugger starts automatically each time the program is launched.
The abuse of utilman.exe is also noteworthy launched directly from the Windows login screen by using Windows logo key + U keyboard shortcutpotentially allowing threat actors to configure backdoors via Image File Execution Options Registry key.
“Close inspection of the SFX archive reveals that it functions as a password-protected backdoor by abusing WinRAR’s setup options rather than containing any malware,” explained Minton.
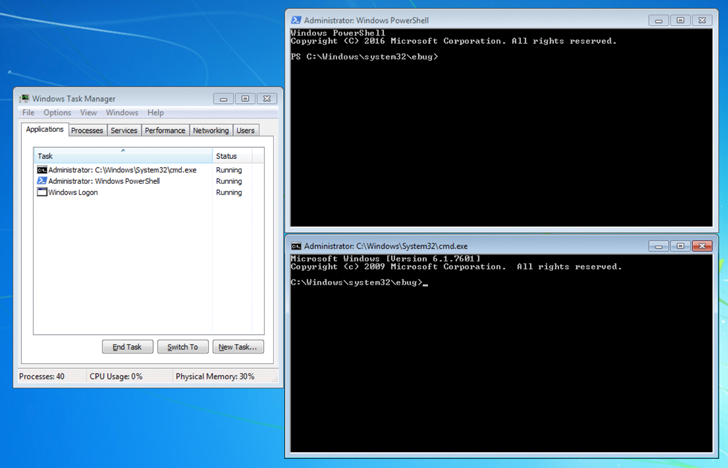
Specifically, the file is engineered to run PowerShell (powershell.exe), Command Prompt (cmd.exe), and Task Manager (taskmgr.exe) with NT AUTHORITY\SYSTEM privileges by providing proper passwords to archives.
“This type of attack is less likely to remain undetected by traditional antivirus software looking for malware in archives (which are often also password protected) than is the behavior of SFX archive decompressor stubs,” Minton added.
Learn to Secure Identity Perimeter – A Proven Strategy
Improve your business security with our upcoming cybersecurity webinar led by our experts: Explore the Identity Perimeter strategy!
This is not the first time SFX files have been used in attacks as a way to keep attackers undetected. In September 2022, Kaspersky disclosed a malware campaign that used links to these password-protected files spread Red Line Thief.
A month later, the popular Emotet botnet was observed delivering an SFX archive which, once opened by the user, would automatically extract a second, password-protected SFX archive, enter the password, and run its contents without further user interaction using a batch script.
To mitigate the threat posed by this attack vector, it is recommended that SFX archives be analyzed through archiving software to identify the potential for assigned scripts or binaries to be extracted and run on executable.
[ad_2]
Source link






