
Israel-based Spyware Company QuaDream Targets High-Risk iPhones with Clickless Exploits
[ad_1]

Threat actors using hacking tools from Israeli surveillance software vendor QuaDream targeted at least five members of civil society in North America, Central Asia, Southeast Asia, Europe and the Middle East.
According to the findings of a group of researchers from Citizen Lab, a spyware campaign was directed against journalists, political opposition figures and NGO workers in 2021. The names of the victims were not disclosed.
It is also alleged that the company abused the no-click exploit nickname END OF THE DAY on iOS 14 to deploy spyware as a zero-day in versions 14.4 and 14.4.2. There is no evidence that the exploit was used after March 2021.
ENDOFDAYS “appears to take advantage of invisible iCloud calendar invitations sent from spyware operators to victims,” the researchers said saidadded an .ics file containing invitations to two events whose dates are backwards and overlapping so as not to alert the user.
The attack is alleged to have taken advantage of a quirk in iOS 14 that any iCloud calendar invitation with a backward time received by the phone is automatically processed and added to the user’s calendar without any notification or request.
The Microsoft Threat Intelligence Team is tracking QuadDream as DEV-0196, describing it as a private sector offensive actor (PSOA). While the cyber mercenary company was not directly involved in the targeting, having been known to sell “exploitation and malware services” to government customers, the tech giants judged it with high confidence.
Malware, named KingsPawncontains the monitoring agent and the main malware agent, both of which are Mach-O files written in Objective-C and Go respectively.
While monitoring agents are responsible for reducing malware forensic footprints to evade detection, lead agents are equipped with capabilities to collect device information, cellular and Wi-Fi data, harvest files, access cameras in the background, access locations, call logs, and iOS Keychain. , and even create iCloud one-time-based (TOTP) passwords.
Other samples support audio recording of phone calls and microphones, running queries in SQL databases, and cleaning up forensic traces, such as deleting all calendar events from two years before the current time. Data is extracted via HTTPS POST requests.
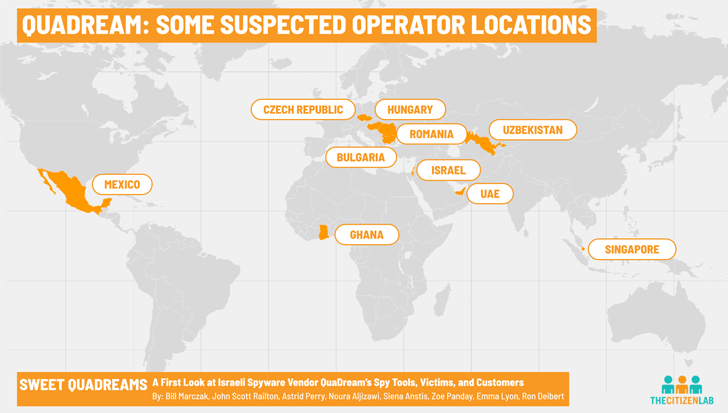
Internet scans conducted by Citizen Lab revealed that QuaDream customers were operating 600 servers from several countries around the world between late 2021 and early 2023, including Bulgaria, Czech Republic, Hungary, Romania, Ghana, Israel, Mexico, Singapore, UAE and Uzbekistan.
Despite efforts by the spyware to cover its tracks, the interdisciplinary lab says it was able to uncover unspecified traces of what it called the “Ectoplasmic Factor” that could be used to track future QuaDream devices.
This isn’t the first time QuaDream has attracted attention. In February 2022, Reuters reported that the company armed the zero-click FORCEDENTRY exploit in iMessage to deploy a spyware solution called REIGN.
Then in December 2022, Meta revealed that a network of 250 fake accounts on Facebook and Instagram controlled by QuaDream had been shut down to infect Android and iOS devices and extract private data.
Learn to Secure Identity Perimeter – A Proven Strategy
Improve your business security with our upcoming cybersecurity webinar led by our experts: Explore the Identity Perimeter strategy!
If anything, the development is another indication that despite the notoriety of the NSO Group, commercial spyware companies continue to fly under the radar and develop sophisticated spyware products for use by government clients.
“Until the uncontrolled proliferation of commercial spyware is managed to be contained through systemic government regulation, the number of abuse cases will likely continue to grow, driven both by companies with recognizable names, and others still operating in the shadows,” said Citizen Lab.
Calling the growth of paid spyware companies a threat to democracy and human rights, Microsoft said combating such offensive actors requires a “collective effort” and “multistakeholder collaboration.”
“Additionally, it’s only a matter of time before the use of the tools and technology they sell spreads even further,” Amy Hogan-Burney, general counsel for the company’s association for cybersecurity policy and protection, said.
“This poses a real risk to human rights online, but also to the security and stability of the wider online environment. The services they offer require cyber mercenaries to stockpile vulnerabilities and find new ways to access networks without authorization.”
[ad_2]
Source link






