
Growing Cybercrime Groups Targeting Businesses with Ransomware
[ad_1]
Cybersecurity researchers have detailed the tactics of an “rising” gang of cybercriminals called “Read The Manual” (RTM) Lockers that function as private ransomware-as-a-service (RaaS) providers and carry out opportunistic attacks to generate illegal profits.
“The ‘Read The Manual’ Locker gang uses affiliates to ransom victims, all of whom are forced to comply with the gang’s strict rules,” cybersecurity firm Trellix said in a statement. report shared with The Hacker News.
“The group’s business-like setting, where affiliates are required to remain active or notify the gang of their leave, demonstrates the organizational maturity of the group, as has also been observed in other groups, such as Conti.”
RTMfirst documented by ESET in February 2017, started in 2015 as banking malware targeting businesses in Russia via drive-by downloads, spam, and phishing emails. The chain of attacks was set up by the group from then on evolve to deploy the ransomware payload on compromised hosts.
In March 2021, the Russian-speaking group associated to a blackmail and extortion campaign that propagated three threats, including financial trojans, legitimate remote access tools, and a type of ransomware called quote.
Trellix told The Hacker News that there is no connection between Quoter and the RTM Locker ransomware executable used in the latest attack.
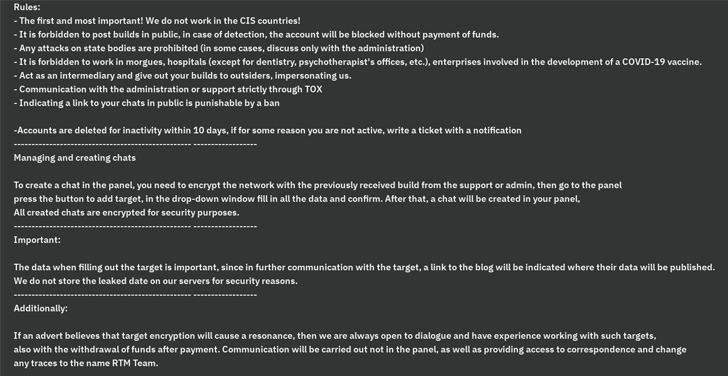
A key feature of the threat actor is its ability to operate in the shadows by deliberately avoiding high-profile targets that may draw attention to its activities. To that end, CIS countries, as well as morgues, hospitals, COVID-19 vaccine related companies, critical infrastructure, law enforcement and other leading companies are barred from the group.
“The goal of RTM gangs is to attract as little attention as possible, where rules help them avoid high-value targets,” said security researcher Max Kersten. “Their affiliate management to achieve that goal required some level of sophistication, though it wasn’t a high level.”
Master the Art of Dark Web Intelligence Gathering
Learn the art of extracting threat intelligence from the dark web – Join this expert-led webinar!
RTM Locker malware builds are bound by strict mandates that prohibit affiliates from leaking samples, or risk facing a ban. Among the other rules set out is a clause that locks out affiliates if they remain inactive for 10 days without prior notice.
“The attempts by the gang to avoid attracting attention are most unusual,” explains Kersten. “Affiliates also need to be active, making it more difficult for researchers to infiltrate gangs. Overall, gang-specific effort in this area is higher than what is typically observed compared to other ransomware groups.”
It is suspected that the lockers were run on a network that was already under enemy control, suggesting that the system may have been compromised by other means, such as a phishing attack, malspam, or exploiting a vulnerable server exposed to the internet.
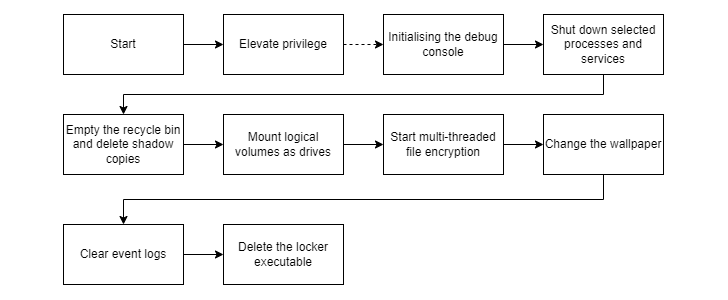
Threat actors, like other RaaS groups, use extortion techniques to force victims to pay. The payload, for its part, is capable of elevating privileges, stopping antivirus and backup services, and deleting shadow copies before starting the encryption procedure.
It’s also designed to empty the Recycle Bin to prevent restores, change the wallpaper, delete event logs, and run shell commands that self-delete lockers as a final step.
The findings suggest that cybercrime groups will continue to “adopt new tactics and methods to circumvent the headlines and help them fly under the radar of researchers and law enforcement,” said Kersten.
[ad_2]
Source link






