
Hackers Exploit Outdated WordPress Plugin to Backdoor Thousands of WordPress Sites
[ad_1]

Threat actors have been observed utilizing legitimate but outdated WordPress plugins to surreptitiously backdoor websites as part of an ongoing campaign, Sucuri revealed in a report published last week.
The plugin in question is Eval PHP which was released by a developer called flashpixx. This allows users to enter PHP code pages and WordPress site posts which are then executed whenever the post is opened in a web browser.
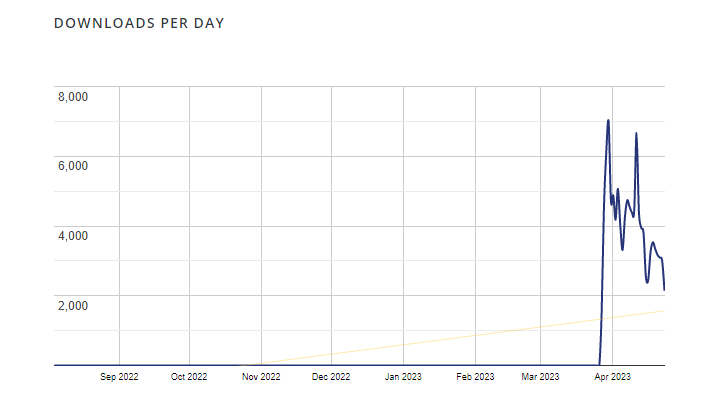
When PHP Evaluation having not received an update in 11 years, statistics compiled by WordPress show that it was installed on more than 8,000 websites, with the number of downloads skyrocketing from an average of one or two since September 2022 to 6,988 as of March 30, 2023.
On April 23, 2023 alone, it has been downloaded 2,140 times. This plugin has accumulated 23,110 downloads over the last seven days.
GoDaddy-owned Sucuri said it observed several databases of infected websites that were injected with malicious code into table “wp_posts”.which stores the site files posts, pages, and navigation menus information. The requests come from three different IP addresses based in Russia.
“The code is quite simple: using file_put_contents function to build PHP scripts into a website’s docroot with a defined remote code execution backdoor,” said security researcher Ben Martin.
“While the intended injection does not insert conventional backdoors into the file structure, the combination of legitimate plugins and backdoor droppers in WordPress posts allows them to easily re-infect websites and remain hidden. All an attacker needs to do is visit one of the infected posts or pages and the backdoor will be injected into the file structure.”
Sucuri says it has detected more than 6,000 instances of this backdoor on compromised websites in the past 6 months, describing the pattern of injecting malware directly into databases as “a new and exciting development.”
Zero Trust + Deception: Learn How to Outsmart Attackers!
Discover how Fraud can detect advanced threats, stop lateral moves, and improve your Zero Trust strategy. Join our insightful webinar!
The attack chain requires installing the Eval PHP plugin on a compromised site and abusing it to create persistent backdoors across multiple posts which are also sometimes saved as drafts.
“How the Eval PHP plugin works simply save the page as a draft to execute the PHP code inside (evalphp) shortcodes,” Martin explained, adding the rogue page was created with the real site administrator as the author, indicating the attacker was successfully logged in as a privileged user.
The developments once again show how bad actors are experimenting with various methods to maintain their foothold in compromised environments and circumvent server-side scans and file integrity monitoring.
Site owners are advised to secure WP Admin Dashboard and watch out for suspicious logins to prevent threat actors from gaining admin access and installing plug-ins.
[ad_2]
Source link






