
Google Gets Court Order to Remove CryptBot Infecting Over 670,000 Computers
[ad_1]
Google on Wednesday said it had obtained a temporary US court order to interfere with the distribution of Windows-based information-stealing malware CryptBot and “slow down” its growth.
Tech giant Mike Trinh and Bureau Pierre-Marc said the effort is part of steps needed to “hold accountable not only the malware’s criminal operators, but also those who profit from its distribution.”
CryptBot is estimated to have infected more than 670,000 computers in 2022 with the aim of stealing sensitive data such as authentication credentials, social media account logins and cryptocurrency wallets from Google Chrome users.
The harvested data is then extracted to the threat actor, who then sells the data to other attackers for use in data breach campaigns. CryptBot first first time found in the wild in December 2019.
Malware is usually delivered via maliciously modified packaged versions of legitimate and popular software such as Google Earth Pro and Google Chrome hosted on bogus websites.
What’s more, the CryptBot campaign unearthed by Red Canary in December 2021 required the use of KMSPico, an unofficial tool used to illegally activate Microsoft Office and Windows without a license key, as a delivery vector.
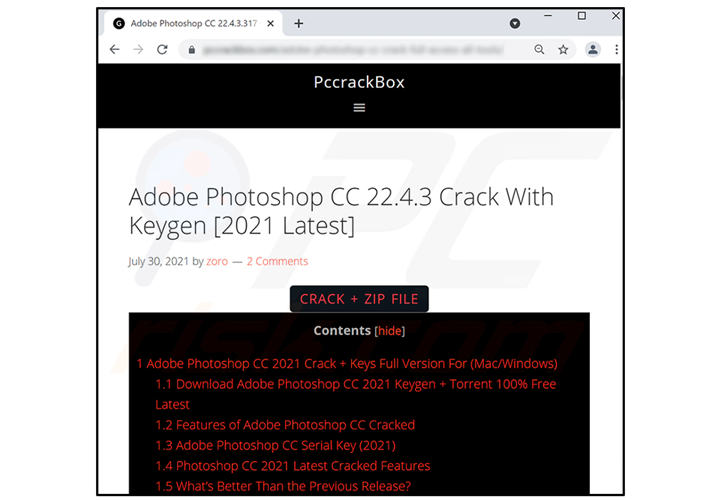
Then in March 2022, BlackBerry disclosed details of new and improved versions of the rogue infostealer distributed via compromised pirate sites purporting to offer “cracked” versions of various software and video games.
The main distributor of CryptBot, per Google, allegedly operates a “worldwide criminal enterprise” based in Pakistan.
Google said it would use the court order, granted by a federal judge in the Southern District of New York, to “revoke current and future domains associated with the distribution of CryptBot,” thereby preventing the spread of new infections.
Zero Trust + Deception: Learn How to Outsmart Attackers!
Discover how Fraud can detect advanced threats, stop lateral moves, and improve your Zero Trust strategy. Join our insightful webinar!
To reduce the risk posed by such threats, it is advised to only download software from well-known and trustworthy sources, check reviews and ensure that the operating system and device software are kept up to date.
The disclosure comes weeks after Microsoft, Fortra, and the Health Information Sharing and Analysis Center (Health-ISAC) officially joined hands to take down servers hosting illegal copies of Cobalt Strike to prevent abuse of the tool by threat actors.
It also follows Google’s attempt to shut down the command-and-control infrastructure associated with a botnet dubbed Grupteba in December 2021. However, the malware resurfaced six months later as part of an “upgrade” campaign.
[ad_2]
Source link






