
New Decoy Dog Malware Toolkit Revealed: Targeting Enterprise Networks
[ad_1]
Analysis of over 70 billion DNS records has led to the discovery of a new advanced malware tool dubbed Charming Dog target enterprise network.
Charming Dogas the name suggests, circumvents and employs techniques such as strategic domain aging and DNS query dribbling, in which a series of queries is transmitted to a command-and-control (C2) domain so as not to arouse suspicion.
“Decoy Dog is a cohesive toolkit with a number of very unusual characteristics that make it uniquely identifiable, especially when checking its domain at the DNS level,” Infoblox said in an advisory published late last month.
The cybersecurity firm, which identified the malware in early April 2023 after anomalous DNS beaconing activity, said its unusual characteristics allowed it to map additional domains that are part of the attack infrastructure.
That said, use of Decoy Dog in the wild is “extremely rare”, with DNS signatures matching less than 0.0000027% of the internet’s 370 million active domains, according to the California-based company.
One of the main components of the toolkit is Pupy RAT, an open source trojan that is delivered via a method called DNS tunnelwhere the DNS query and response are used as C2 to silently drop the payload.
It should be noted that cross-platform use of Pupy RAT has been linked to nation-state actors from China such as Earth Berberoka (aka GamblingPuppet) in the past, although there is no evidence to suggest the actor’s involvement in this campaign.
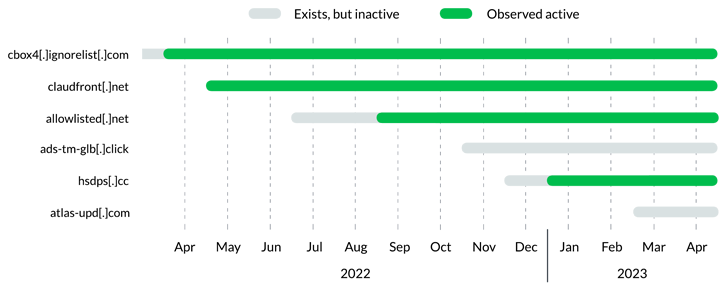
Further investigation of Decoy Dog showed that the operation had taken place at least a year prior to its discovery, with three different infrastructure configurations detected to date.
Learn How to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
Another important aspect is the unusual DNS beaconing behavior associated with the Decoy Dog domain, such that they adhere to a periodic, but infrequent pattern of DNS requests, thus flying under the radar.
“Enchanted dog domain can be grouped together based on shared registrars, nameservers, IPs, and dynamic DNS providers,” said Infoblox.
“Given other similarities between the Decoy Dog domains, this suggests either one threat actor is gradually evolving their tactics, or multiple threat actors are using the same device on different infrastructures.”
[ad_2]
Source link







