
Researchers Find 3 Vulnerabilities in Microsoft Azure API Management Service
[ad_1]

Three new security flaws have been disclosed in the Microsoft Azure API Management service which can be abused by bad actors to gain access to sensitive information or backend services.
These include two server-side request forgery (SSRF) flaws and one instance of unlimited file upload functionality in the Management API developer portal, according to Israeli cloud security firm Ermetic.
“By abusing the SSRF vulnerability, an attacker can send requests from the CORS Proxy service and the hosting proxy itself, access internal Azure assets, deny service, and bypass web application firewalls,” security researcher Liv Matan said in a statement. report shared with The Hacker News.
“By traversing file upload paths, attackers can upload malicious files to Azure hosted internal workloads.”
Azure API management is a multicloud management platform which enables organizations to securely expose their API to external and internal customers and enable a variety of connected experiences.
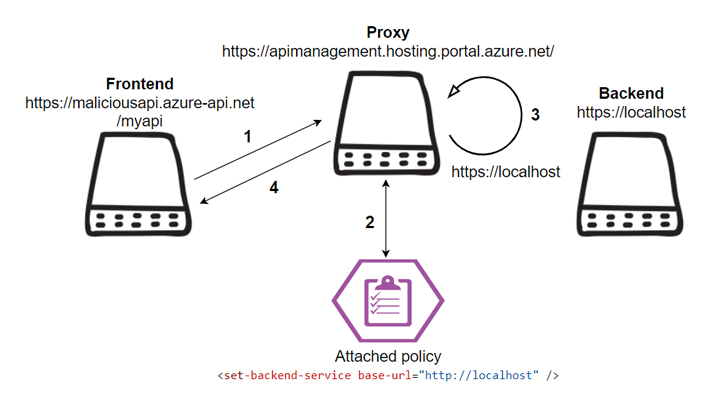
Of the two SSRF weaknesses identified by Ermetic, one is a shortcut for a fix made by Microsoft to address a similar vulnerability reported by Orcas earlier this year. Another vulnerability resides in the Management API’s proxy function.
SSRF vulnerability exploits can results loss of confidentiality and integrity, allowing threat actors to read internal Azure resources and executing unauthorized code.
The path traversal flaw found in the developer portal, on the other hand, stems from a lack of validation of file types and uploaded file paths.
Authenticated users can take advantage of this vulnerability to upload malicious files to developer portal servers and potentially even execute arbitrary code on the underlying system.
Learn How to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
After responsible disclosure, all three flaws have been patched by Microsoft.
The findings come weeks after researchers from Orca detailed “design flaws” in Microsoft Azure could be exploited by attackers to gain access to storage accounts, move laterally in environments, and even execute remote code.
It also follows the discovery of another Azure vulnerability dubbed EmojiDeploy that could allow attackers to seize control of targeted applications.
[ad_2]
Source link







