
Hackers Target Italian Corporate Banking Clients with DrIBAN’s New Web Injection Tool
[ad_1]

An Italian corporate banking client is the target of an ongoing financial fraud campaign that has taken advantage of a new web injection tool called drIBAN at least since 2019.
“The main objective of the drIBAN fraudulent operation was to infect Windows workstations within the corporate environment trying to tamper with the legitimate banking transfers made by the victims by changing recipients and transferring money to unauthorized bank accounts,” Cleafy researchers Federico Valentini and Alessandro Strino said.
Bank accounts, according to an Italian cybersecurity firm, are controlled by the threat actor himself or an affiliate, who is then tasked with laundering the stolen funds.
The use of web injection is a time-tested tactic that allows malware to inject custom scripts on the client side via man-in-the-browser (MitB) attacks and intercept traffic to and from servers.
Fraudulent transactions are often carried out using a technique called an Automated Transfer System (ATS) that is able to pass through anti-fraud system enforced by banks and initiating an unauthorized wire transfer from the victim’s own computer.
Over the years, the operators behind drIBAN have become increasingly adept at evading detection and developing effective social engineering strategies, in addition to establishing a foothold for a long time in corporate bank networks.
Cleafy says 2021 is the year the quintessential “banking trojan” operation evolves into an ongoing threat. In addition, there are indications that the activity cluster overlaps with a 2018 campaign installed by an actor tracked by Proofpoint as TA554 targeting users in Canada, Italy and the UK
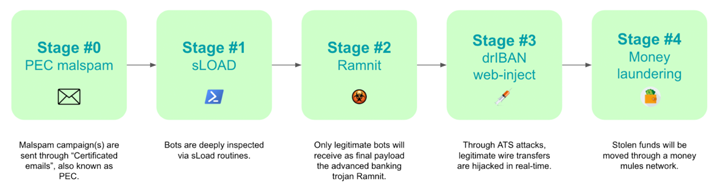
The attack chain starts with a certified e-mail (or PEC emails) in an attempt to lull victims into a false sense of security. These phishing emails come with an executable file that acts as a malware downloader called load (aka Starslord loader).
The PowerShell loader, sLoad is a reconnaissance tool that gathers and extracts information from compromised hosts, with the aim of assessing targets and dropping more significant payloads such as Ramnit if the target is deemed profitable.
“This ‘enrichment phase’ can continue for days or weeks, depending on the number of infected machines,” said Cleafy. “Additional data will be extracted to make the resulting botnet even more solid and consistent.”
Learn How to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
sLoad also makes use of living-off-the-land (ManyL) techniques by abusing legitimate Windows tools like PowerShell And BITSAdmin as part of his avoidance mechanism.
Another characteristic of this malware is its ability to check a predefined list of corporate banking institutions to determine if the hacked workstation is one of the targets, and if so, proceed with infection.
“All bots that successfully pass these steps will be selected by the botnet operators and considered as ‘new candidates’ for banking fraud operations moving forward to the next stage, where Ramnit, one of the most sophisticated banking trojans, will be installed,” he said. . said the researcher.
[ad_2]
Source link







