
US Government Neutralizes Russia’s Most Advanced Snake Cyber Espionage Tool
[ad_1]

The US government on Tuesday announced a formal court breakdown of global networks compromised by a sophisticated type of malware known as Snake used by the Federal Security Service (FSB) of Russia.
Snake, which has been dubbed “the most advanced cyber-espionage tool”, is the work of a Russian state-sponsored group called Turla (aka Iron Hunter, Secret Blizzard, SUMMIT, Uroburos, Venomous Bear, and Waterbug), which the US government considers a unit in the Central 16 FSB.
The perpetrator of the threat has a track record focuses heavily on entities in Europe, the Commonwealth of Independent States (CIS), and NATO-affiliated countries, with recent activity expanding its footprint to include Middle Eastern countries perceived to be a threat to countries it supports by Russia in the region.
“For nearly 20 years, this unit (…) has used a version of the Snake malware to steal sensitive documents from hundreds of computer systems in at least 50 countries, belonging to North Atlantic Treaty Organization (NATO) member governments, journalists, and other targeted targets. of interest to the Russian Federation,” the Ministry of Justice said.
“After stealing these documents, Turla extracted them through a secret network of computers compromised by Snake in the United States and around the world.”
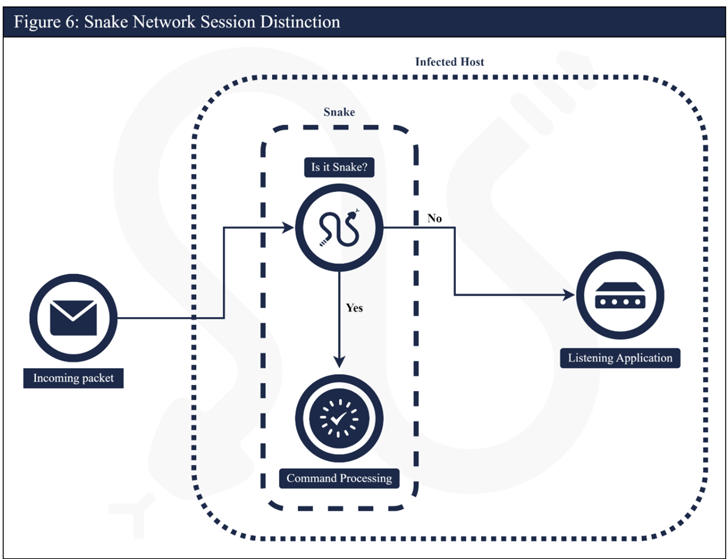
The neutralization was orchestrated as part of an effort dubbed Operation MEDUSA through a tool created by the US Federal Bureau of Investigation (FBI) codenamed PERSEUS that allows authorities to issue commands to malware causing it to “overwrite its own vital components” on infected machines.
The self-destruct instructions, engineered after decrypting and decoding the malware’s network communications, caused “the Snake implant to deactivate itself without affecting the host computer or legitimate applications on the computer,” the agency said.
Snakes, according to a advisor released by the US Cybersecurity and Infrastructure Security Agency (CISA), designed as a covert tool for long-term intelligence gathering on high-priority targets, allowing adversaries to create peer-to-peer (P2P) networks of compromised systems around the World.
Moreover, multiple systems in the P2P network serve as relay nodes to route covert operational traffic to and from Snake malware embedded in key FSB targets, making such activity difficult to detect.
Subsequent C-based cross-platform malware uses specific communication methods to add a new layer of stealth and features a modular architecture that allows for an efficient way to inject or modify components to augment their capabilities and maintain continuous access to valuable information.
“Snake demonstrates careful software engineering design and implementation, with an implant that is surprisingly few bugs given its complexity,” CISA saidadding an initial version of the implant was developed around early 2004.
“The name Uroburos is fitting, as the FSB cycles it through nearly constant stages of upgrading and rebuilding.”
Learn How to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
Infrastructure linked to Kremlin-backed groups has been identified in more than 50 countries across North America, South America, Europe, Africa, Asia and Australia, although the targeting is seen as more tactical, including government networks, research facilities and journalists. .
Sectors that fell victim in the US included education, small business, and media organizations, as well as critical infrastructure sectors such as government facilities, financial services, essential manufacturing, and communications.
Despite these setbacks, Turla remains an active and formidable adversary, dishing out an array of tactics and tools to penetrate his targets across Windows, macOS, Linux, and Android.
This development comes less than a year after US intelligence and law enforcement agencies dismantled a modular botnet known as Cyclops Blink that was controlled by another Russian nation-state actor known as Sandworm.
[ad_2]
Source link







