
Iranian Hackers Use SimpleHelp Remote Support Software for Persistent Access
[ad_1]
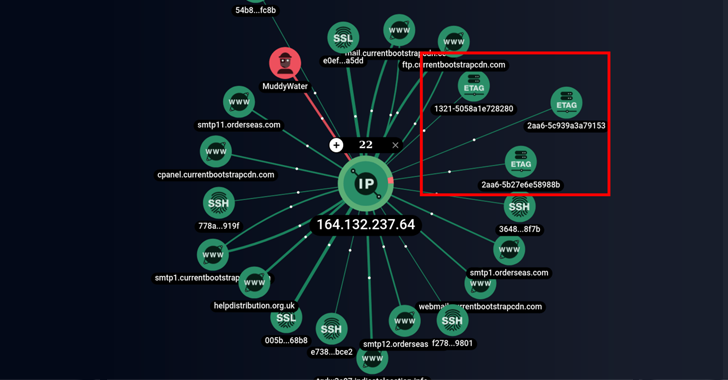
The Iranian threat actor known as MuddyWater continues a time-tested tradition of relying on legitimate remote administration tools to seize targeted systems.
While the nation-state group has previously used ScreenConnect, RemoteUtilities, and Syncro, a new analysis from Group-IB has disclosed adversary use of its SimpleHelp remote support software in June 2022.
MuddyWater, active since at least 2017, is considered a subordinate element within Iran’s Ministry of Intelligence and Security (MOIS). Some of the main targets include Turkey, Pakistan, UAE, Iraq, Israel, Saudi Arabia, Jordan, US, Azerbaijan and Afghanistan.
“MuddyWater uses SimpleHelp, a legitimate remote device management and control tool, to ensure persistence on victim devices,” said Nikita Rostovtsev, senior threat analyst at Group-IB.
“SimpleHelp was not compromised and was used as intended. Threat actors found ways to download tools from official websites and use them in their attacks.”
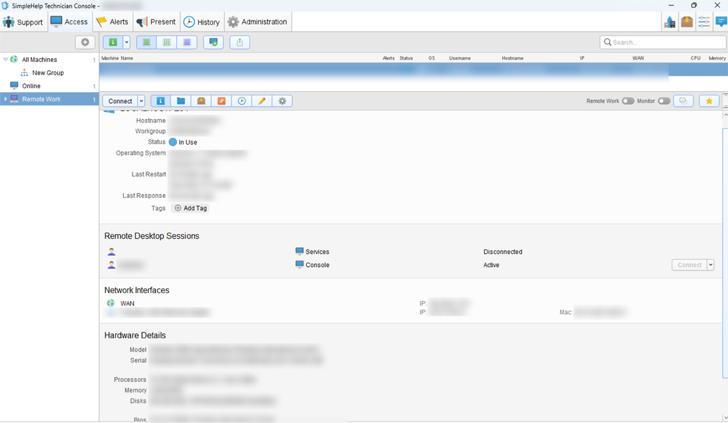
The exact distribution method used to drop the SimpleHelp sample is currently unclear, although the group is known to send spear-phishing messages containing malicious links from compromised corporate mailboxes.
Group-IB findings are strengthened by Slovak cybersecurity firm ESET earlier this January, detailing MuddyWater attacks in Egypt and Saudi Arabia that required the use of SimpleHelp to deploy the Ligolo reverse tunneling tool and credential harvester dubbed MKL64.
Master the Art of Dark Web Intelligence Gathering
Learn the art of extracting threat intelligence from the dark web – Join this expert-led webinar!
The Singapore-headquartered company further said that it was able to identify hitherto unknown infrastructure operated by the group as well as a PowerShell script capable of receiving commands from remote servers, the results of which are sent back to the server.
The disclosure comes weeks after Microsoft detailed the group’s modus operandi for carrying out destructive attacks on hybrid environments under the guise of ransomware operations.
[ad_2]
Source link






