
Chinese Hacking Group Earth Longzhi Reemerges with Sophisticated Malware Tactics
[ad_1]
China’s state-sponsored hacking outfit has resurfaced with a new campaign targeting government, healthcare, technology and manufacturing entities based in Taiwan, Thailand, the Philippines and Fiji after more than six months of inactivity.
Micro Trends associated the intrusion is set to a cyber espionage group which it tracks by name Longzhi Earthwhich is a subgroup within APT41 (aka HOODOO or Winnti) and shares overlap with various other clusters known as Earth Raw, SparklingGoblin, and GroupCC.
Earth Longzhi was first documented by the cybersecurity firm in November 2022, detailing its attacks on organizations located in East and Southeast Asia and Ukraine.
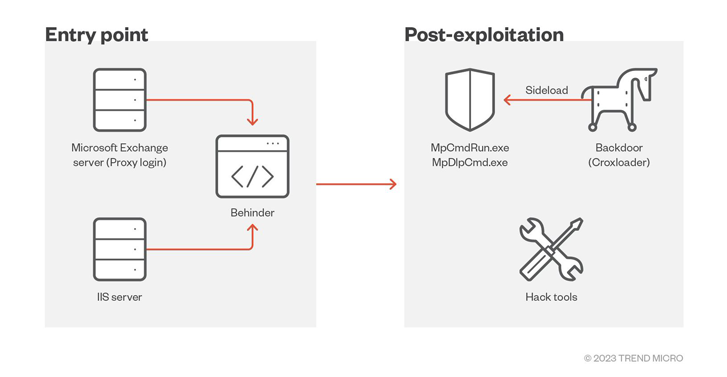
Attack chains deployed by threat actors leverage vulnerable public applications as entry points to deploy the BEHINDER web shell, and then leverage that access to drop additional payloads, including a new variant of the Cobalt Strike loader called CroxLoader.
“A recent campaign (…) abused the Windows Defender executable to sideload DLLs while also exploiting a vulnerable driver, zamguard.sys, to disable security products installed on hosts via a bring your own vulnerable driver (BYOVD) attack ,” said Trend Micro.
This is by no means the first time that Earth Longzhi has leveraged the BYOVD technique, with the previous campaign using the vulnerable RTCore64.sys driver to limit the implementation of security products.
The malware, dubbed SPHijacker, also uses a second method it refers to as “stack rumble” to achieve the same goal, which requires changes to the Windows Registry to interrupt process execution flows and intentionally cause targeted applications to crash on launch.
“This technique is a type of (denial-of-service) attack that abuses the undocumented MinimumStackCommitInBytes value in (Image File Execution Options) registry key,” explains Trend Micro.
“The MinimumStackCommitInBytes value associated with a specific process in the IFEO registry key will be used to determine the minimum stack size that must be performed in initializing the main thread. If the stack size is too large, this will trigger a stack overflow exception and terminate the current process.”
Twins approaches are not the only methods that can be used to undermine security products. Deep Instinct last month detailed its newly christened code injection technique Dirty Vanity which exploits the remote forking mechanism in Windows to blind endpoint detection systems.
What’s more, the driver payload is installed as a kernel-level service using Microsoft’s Remote Procedure Call (RPC) as opposed to the Windows API to avoid detection.
Learn How to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
Also observed in the attack was the use of a DLL-based dropper named Roxwrapper to deliver another Cobalt Strike loader labeled BigpipeLoader as well as a privilege escalation tool (dwm.exe) that abused Windows Task Scheduler to launch a specific payload with SYSTEM privileges.
The specified payload, dllhost.exe, is a downloader capable of taking next-stage malware from an actor-controlled server.
It is worth mentioning here that dwm.exe is based on open source proof-of-concept (PoC) available on GitHubshows that threat actors are taking inspiration from existing programs to hone their malware arsenal.
Trend Micro further said it identified decoy documents written in both Vietnamese and Indonesian, indicating the potential for efforts to target users in both countries in the future.
“Earth Longzhi remains active and continues to improve its tactics, techniques and procedures (TTP),” said security researchers Ted Lee and Hara Hiroaki. “Organizations must remain vigilant against the continued development of new stealth schemes by cybercriminals.”
[ad_2]
Source link







